Cybersecurity researchers have uncovered a sophisticated malware campaign dubbed “Solana-Scan” that targets explicitly cryptocurrency developers in the Solana ecosystem through malicious npm packages.
The attack appears to primarily affect Russian developers, utilizing advanced information-stealing capabilities to harvest cryptocurrency credentials and wallet files.
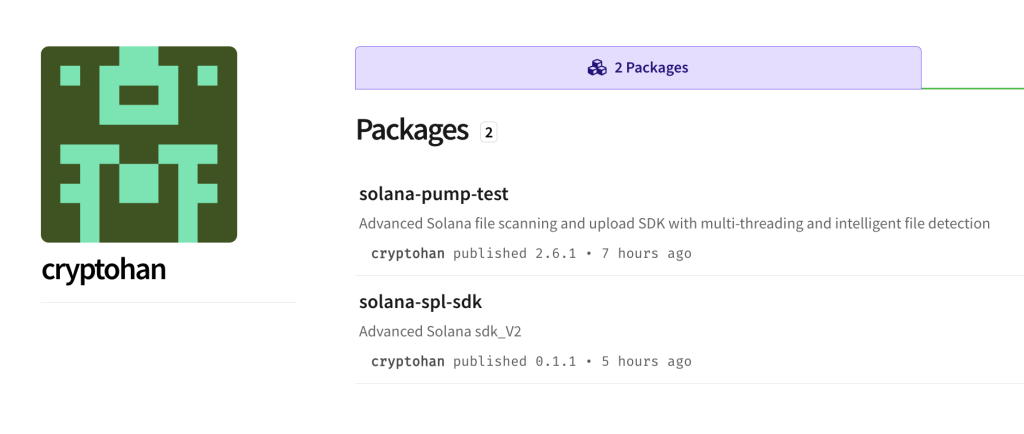
Multi-Package Attack Vector Discovered
Security researchers identified three malicious npm packages published by a threat actor using the handle “cryptohan” and email address [email protected].
The packages “solana-pump-test,” “solana-spl-sdk,” and the now-removed “solana-pump-sdk” masqueraded as legitimate Solana SDK scanning tools to deceive developers into installation.
The malicious packages contain heavily obfuscated JavaScript files that execute a two-stage payload. The initial universal-launcher.js script collects environmental data, including usernames, working directories, and npm installation methods.
Notably, the code contains console.log messages with emojis, suggesting the malware may have been developed using AI code generation tools like Claude.
The second-stage payload systematically scans compromised systems for sensitive files across user directories, including Documents, Downloads, and Desktop folders.
The malware targets files with specific extensions, including .env, .json, .one, .txt, and others, using regular expressions to identify cryptocurrency tokens and credentials.
Command and Control Infrastructure Exposed
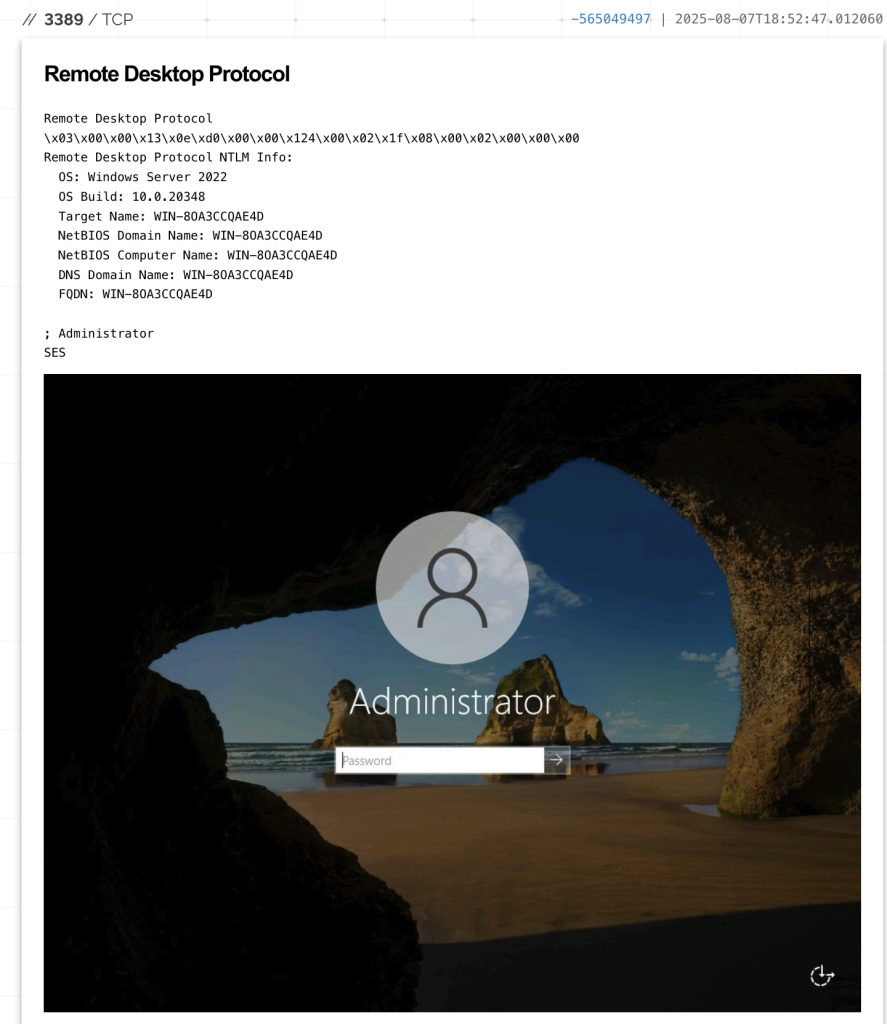
The stolen data is exfiltrated to IP address 209.159.159.198 on port 3000, hosted on a Windows Server 2022 instance in the United States.
Unusually, the command and control server’s web interface at http://209.159.159.198:3000 exposes victim data, including password files, crypto exchange credentials, and wallet files, providing researchers with rare visibility into the operation’s scope.
Analysis of the exposed data reveals victims appear to be primarily located in Moscow, Russia, based on IP geolocation data. This geographic targeting, combined with the US-based infrastructure, raises questions about potential state-sponsored involvement.
Detection and Mitigation
The campaign began on August 15, 2025, at 07:37 UTC with 14 package versions published over 10 hours. Key indicators of compromise include the malicious package names, file hashes of the JavaScript payloads, and the command and control IP address.
Traditional security tools, including Software Composition Analysis (SCA) and Endpoint Detection and Response (EDR) solutions, may not effectively detect this type of supply chain attack.
Organizations should implement real-time package scanning solutions and maintain updated dependency inventories.
The Solana-Scan campaign represents an evolution in supply chain attacks, demonstrating threat actors’ increasing sophistication in targeting specific developer communities and their improved understanding of npm and Node.js environments for payload delivery.
Indicators of Compromise (IOCs)
NPM Packages:
solana-pump-test
solana-spl-sdk
solana-pump-sdk
Files
bd93bea65242bc8205728f129c9bbadc694d849a028fc2d771f9ea60a293665c ./index.cjs
e6f75dbf6d42e4c34b1a267426accd6dfd3ea7773a28e580c10687768fcc3883 ./index.js
ed5b9c8bfede0668a240e976e65a46e2dd393ef597c7068c1bb842173ae51ebb ./install.cjs
233a408bbcd072236d9331792356ed0b59da5a4c51e3ca74f860a4bf1a621c15 ./install.js
21a6135067c3f150a4629e4746c8b81c5b41567117eeaf69224a1919077521d9 ./universal-launcher.cjs
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates